Block exchange online email on unmanaged devices
- Anand P
- Feb 2, 2023
- 2 min read
Hello All, In this blog I will guide you on how to block users from configuring their work email on native email clients on unmanaged devices (which are not managed or enrolled to Intune) and force users to use the App protection managed application for example Outlook Application.
Organizations may require users to use outlook as their email client to ensure the organization's data is secure when used on an unmanaged device. Conditional access policies allow us to achieve this by blocking users from configuring their native email client on personally owned and unmanaged devices and allowing users to configure if the device is managed or enrolled to Intune, as a result, organizations can protect their data.
Let's see how we can accomplish this, we will configure a conditional access policy to restrict users from configuring their corporate email on their native email application and only allow them to use Outlook
Create a conditional access policy
Step 1: Sign in to the Endpoint manager Link, and navigate to conditional access

Step 2: Select New Policy from the conditional access policy page

Step 3: Name the Policy, which should be a relevant name for understanding purposes, and select All users under Assignments. Select the Exclude option and select the account or directory role you wish to exclude from the policy. For all users under Assignments, for excluding a glass break account from the policy please select Exclude option and select the account or directory role you would like to exclude.

Step 4: Select the application for which conditional access will be applied: tap on Cloud apps or actions, tap on select apps -> tap on select applications

now search for exchange online, and you can see the application names Office 365 ExchangeOnline select the application and tap on Then search for exchange online, and you will see the application names Office 365 ExchangeOnline, click on that application, and then select it.

As a result, the respective application will be selected and you can see it in the list

Step 5: Select the device platform on which the policy should be applied by tapping on Conditions and selecting the platform.

In Configure, toggle to yes and select Android and iOS and then tap on Select.

Step 6: Choosing the device platform will allow us to create access enforcement. You can choose whether to block or grant access by selecting Grant access, selecting Require approved client apps and Require app protection policy, and selecting Require all selected controls. Once selected, conditional access appears under Enable Policy in Report-Only.
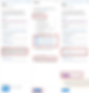
To create a conditional access policy, toggle that to On and tap on create

The policy has now been created.

Users can't sign in to email clients not included in the App Protection Policy or not approved applications. They will receive the below error message.

Conclusion
The purpose of this article is to explain how to configure a conditional access policy so that users cannot configure their mailboxes on email clients which are not approved or not protected by app protection, but rather on approved email clients like Outlook, for example.

